In this series of blogs, we are looking at the practice of using a fraud audit to detect shell company schemes occurring in an accounts payable file. Because the practice of effective fraud auditing is grounded in knowledge, we will start with a knowledge section and then delve into a demonstration of the fraud audit process.
Trivia Answers
As an accountant, you must be familiar with the terms, debits, and credits, so here are a few questions to test your accounting knowledge. What is the word origin of debits and credits?Latin, debere and credre. Did you ever wonder why the abbreviation of debit is DR. yet the English term (debit) has no “r.” The reason is the abbreviation evolved from the Latin term, debere.
Who created the phrase "debits and credits"? Luca Paciolli
On which printing press was the first book on double-entry accounting printed? Gutenberg Press
What is the definition of “debere?” To owe
What is the definition of “credre?” To entrust
Mastering Shell Company Detection: Practical Steps for Fraud Auditors (Part 4)
Knowledge Section
What are the forms of business ownership in China?
Among the preferred types of companies in China, investors choose to open a Partnership Enterprise (PE), a Joint Venture (JV), a Wholly Foreign Owned Enterprise (WFOE), a State-Owned Enterprise (SOE), or a Private Enterprise (PE). You can also choose to open a Representative Office (RO) in China.
What is a Chinese limited company?
In a China Limited Liability Company (abbreviated LLC, also known as China Limited Company), the shareholders are solely responsible for the debts of the company with their capital contribution.
How can I check a company in China?
You should check the current status of the company in China's National Enterprise Credit Information Publicity System at http://www.gsxt.gov.cn/index.html, a website of the SAMR.
Business-savvy investors understand the importance of layering companies to minimize legal liability. As you begin your covert research of your vendors, you may determine that your vendor is legally associated with another LLC which is associated with another LLC located in a foreign country. Is this a fraud red flag or just a smart business decision? This is the type of issue you will need to sort out.
Practical Application
As we start, I would refer you to my blog comparing fraud audit to fraud investigation. Note that the only thing that these two concepts have in common is the word fraud.
This next step involves performing covert research on the vendors included in the sample derived from the fraud data analytics. By “covert” we mean information that you can gather without alerting anyone that you are performing a search. Nothing more, nothing less.
The key here is that we’re talking about “research,” not “tick and tie.” Fraud auditing at this stage is about accumulating information to determine if there is credible evidence to formulate an opinion as to whether the vendor has the attributes of a shell company, a conflict-of-interest company, or a commercially viable company. The following is the type of information we gather to formulate our opinions.
1. A/P System check: you are simply gathering information as recorded in your system and determining that the vendor setup complies with your procedures. Be alert to any override red flags.
2. Invoice check: you are examining the invoice for information, invoice number, address, telephone number, website and line-item description. You are also looking for patterns and frequencies of invoice numbers and amounts. Is there a high degree of coincidence?
3. Legal background check: Is the company a registered company? Note names and addresses and compare to your HR database. In particular, compare the incorporation date to the date of the first vendor invoice.
4. Physical address check: the real question is whether the physical address matches a mailbox service, a virtual office, or a professional service provider. Is the address consistent with the type of business?
5. Telephone check: Call the known telephone number and determine if the phone is answered in a business professional manner.
6. Website review: Is the website consistent with a real company, or is the website a one-page website? Are the goods or services on the invoice advertised on the website?
7. Business owner background: Who is the business owner? This can be more difficult to determine than it sounds. Once you have identified the business owner, what can you find out about their professional background, work experience, and credentials?
8. Business capacity: Compare the invoices to the apparent size and ability of the company. The nature of the evidence will vary by the facts and circumstances surrounding the vendor and the contractual relationship the vendor has with your company. Look for advertising, membership in trade organizations, secured debt transactions, proof of insurance, and verification that the company owns assets.
To me, this is the trump card if you are familiar with the card game Pinocle. (Growing up, that card game was a common occurrence in my home, along with pizza on a rectangle pan rather than a round pan.)
Once you have done the research, formulate an opinion on whether or not the examined vendors have the attributes of a shell company. If no, stop. If yes, proceed. Sometimes a picture is worth a thousand words. The following picture is from our training materials:
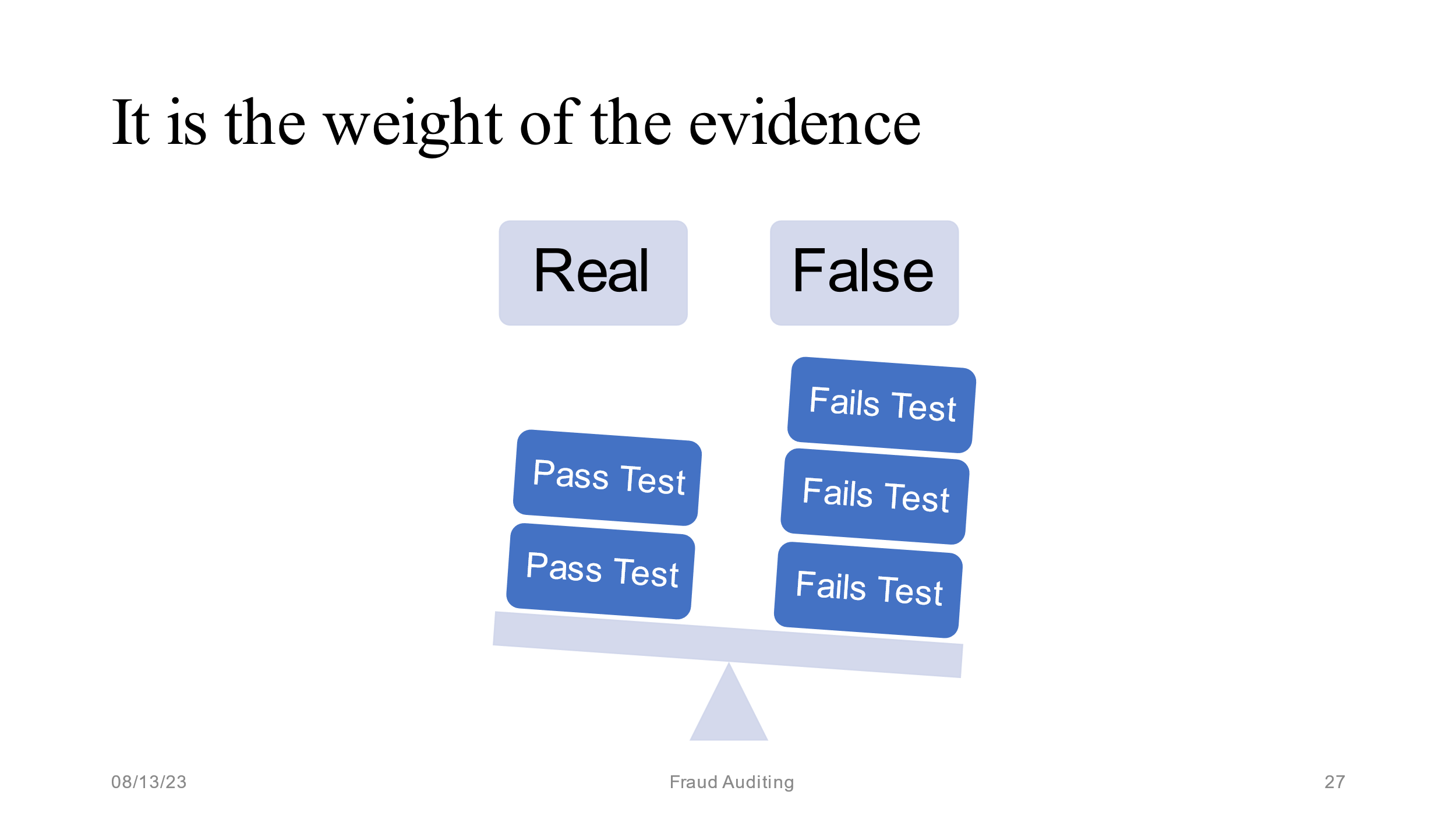
The following represents a sample of conclusion statements we have written after performing the covert research section of our audit program:
Conclusion: Based on the totality of the evidence, there is credible evidence to suggest that vendor does not operate in the marketplace.
Conclusion: Based on the totality of the evidence, there is no credible evidence to suggest the contractor has the characteristics of a contractor open to business for the public or does business with companies other than ours.
Conclusion: Based on the totality of the evidence, there is credible evidence to suggest the services or goods on the invoices were not provided.
Once this is complete, we move on to the next section of our audit program:
-
1. Perform overt research on the fraud action statement.
-
2. Examine internal documents.
-
3. Based on the totality of evidence collected, conduct an interview of the internal person that caused the vendor to be selected.
Trivia: Up Close and Personal With Trivia about Leonard W Vona
- How many Leonard W. Vona’s are in the United States?
- The town of Vona is located in which state in the USA?
- True or false: According to babynamemeaningz.com, Vona is a top trending girl's name.
- True or false: In my first book, I credited the women of my life for my professional success.
- Most visitors to my website are from the USA. What country has the second most visitors?
- From the age of 15 – 30, I actively participated in which sport?




